When done right, outsourcing the cybersecurity and management services that support your operational technology (OT) can unlock speed, scale, and clarity. When done wrong, it can create blind spots, fragility, and dependency.
As buildings become smarter and more connected, the systems that power them—building automation systems (BASs), Internet of Things (IoT) devices, lighting controls, access systems, and more—are now mission-critical. These systems sit outside the traditional informational technology (IT) domain but carry real operational, reputational, and even financial risk.
This leaves many organizations with a challenge: build deep internal capability across a new domain or seek specialized help. Increasingly, leaders are turning to outsourcing the services that manage and secure OT environments to handle the complexity, risk, and opportunity. But like any strategic decision, it comes with tradeoffs.
Why the Trend Toward Outsourcing?
In many organizations, IT departments are already stretched. OT often falls outside their expertise and scope. Meanwhile, operational teams lack the technical background to manage cybersecurity, system architecture, or vendor integrations. The result? Gaps in accountability, inconsistent performance, and missed opportunities.
Outsourcing OT cybersecurity and managed services has become an appealing option. Whether for cybersecurity, system integration, or real-time monitoring, outsourcing can offer clarity and coverage where internal capacity is thin. But it’s not just about patching holes—It’s about driving strategic advantage.
The Benefits: Speed, Scale, and Strategic Leverage
When thoughtfully executed, outsourcing your OT cybersecurity and management needs to a specialized partner can unlock significant value—faster and more consistently than internal teams may be able to achieve alone. The benefits extend well beyond simple efficiency gains:
- Access to Deep OT Expertise: Building systems are a specialized world—marked by legacy protocols, proprietary vendor approaches, and decades-old infrastructure now facing modern cyber threats. OT-specific outsourcing partners bring hard-earned knowledge of how these systems behave, how they fail, and how to secure them. This domain expertise is often hard to develop internally, particularly for lean IT or operations teams already managing competing priorities.
- Accelerated Time-to-Value: With proven playbooks, tools, and platforms, OT outsourcing allows organizations to move quickly from intention to impact. What might take 12–18 months to build internally (if at all) can often be implemented in weeks. This means quicker identification of vulnerabilities, faster rollout of monitoring and reporting, and earlier delivery of insights that improve operational decisions.
- Cost Efficiency Without Corner-Cutting: While it’s tempting to view outsourcing through a budget lens alone, the real cost advantage lies in how services are bundled, standardized, and scaled. By spreading tools and labor across multiple clients or assets, specialized partners can deliver better service at a lower per-building cost without sacrificing depth or quality. Just as importantly, outsourcing avoids the hidden costs of fragmented vendor approaches or missed risk detection.
- Scalable Strategy Across Portfolios: Once an outsourced OT services model proves successful at one site, it can be quickly replicated across a regional or national portfolio. This creates operational consistency, streamlines compliance reporting, and simplifies oversight for property teams and executives alike. Standardized dashboards, service protocols, and risk profiles help decision-makers compare and prioritize investments at the portfolio level.
- Momentum that Lifts Internal Maturity: One of the most strategic—but often underappreciated—benefits of outsourcing is cultural: early success builds belief. When teams begin to see cyber-risk dashboards populate with live data, or can quickly onboard new buildings into a centralized platform, their confidence grows. This momentum elevates internal fluency, enables better decision-making, and prepares the organization to explore more advanced opportunities, such as predictive maintenance, ESG tracking, or energy optimization. Outsourcing doesn’t just fill a gap; it can be a catalyst for organizational growth and maturity.
Pitfalls to Avoid
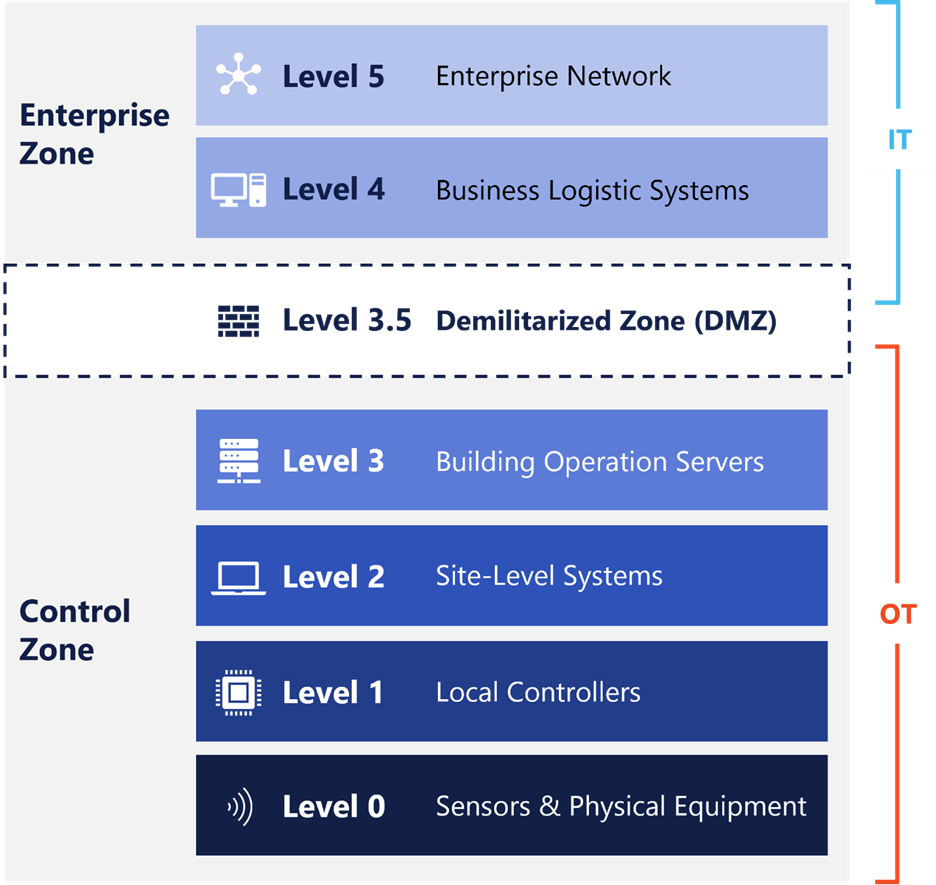
Outsourcing can be powerful, but it’s not a one-size-fits-all solution. To get it right, it’s critical to understand where outsourcing efforts commonly go off course and why. For those unfamiliar, the Purdue Enterprise Reference Architecture is a helpful framework often used to visualize the layers of enterprise and industrial systems. It highlights the challenges of bridging traditional IT (Levels 4–5) and building systems or control networks (Levels 0–3).
Many outsourcing failures happen in that middle ground—the so-called demilitarized zone (DMZ)—where IT strategies alone fall short in operational environments.
Here are some common pitfalls organizations should actively avoid:
- Choosing an IT-Centric Partner: Many well-meaning IT service providers step in to help with building cybersecurity and system visibility, but they often don’t cross the DMZ between IT and OT environments. Their expertise sits squarely in enterprise networks, not the control systems that run HVAC, lighting, elevators, or access control. These systems were not designed with scalable IT architecture in mind, and they often rely on legacy protocols or configurations that require OT-specific understanding. Without this context, IT-led solutions risk missing vulnerabilities, creating false confidence, or even introducing operational risk.
- Loss of Transparency and Control: In some outsourced models, visibility into system health, alerts, and risk levels stays with the vendor—not your internal team. Over time, this can create a dependency where you’re unsure what’s being done or where your greatest risks are. Effective outsourcing should empower your internal teams, not isolate them. Ensure that any partner provides access to dashboards, reporting, and audit trails so you remain in the driver’s seat.
- Overdependence Without Internal Champions: Outsourcing isn’t a replacement for internal ownership. Without clearly designated leaders on your side—whether in operations, IT, or asset management—outsourced services can become disconnected from business goals. Knowledge gaps widen, internal capabilities stall, and vendors end up setting the strategy. A healthy outsourcing model includes upskilling your team over time and aligning service delivery to your evolving needs.
- Outsourcing Without a Verified Foundation: It’s tempting to outsource quickly when under pressure, but if your digital asset inventory is unclear, you may be outsourcing a moving target. You can’t protect or optimize what you don’t know you have. A verified system inventory should precede or accompany any outsourcing effort. It’s the blueprint for effective risk management, performance improvement, and future digital initiatives.
- Misaligned Incentives and Scope Drift: Even experienced vendors can fall into the trap of delivering what’s easiest or most profitable rather than what’s most impactful. If your success metrics aren’t clearly defined, and if you’re not reviewing performance regularly, scope drift and misalignment can creep in. Ensure your vendor’s priorities stay tied to your strategic goals, whether that’s tenant satisfaction, risk reduction, ESG alignment, or portfolio insights.
Final Thoughts
Outsourcing your OT cybersecurity and management isn’t about handing over the keys—It’s about choosing the right copilots. The right partner doesn’t replace your team; they empower it. With early success, you create internal momentum and maturity. With visibility and alignment, you avoid dependency. And with scale, you unlock real strategic leverage.
The buildings may be smart, but smart outsourcing makes the whole portfolio smarter.
Our IntelliNet Managed Service is purpose-built to address the challenges outlined above. From real-time system inventory to OT-specific cybersecurity and scalable dashboards, IntelliNet enables organizations to gain immediate visibility, reduce risk, and accelerate operational maturity across their portfolios. Whether you’re exploring outsourcing for the first time or looking to enhance existing efforts, we’d love to connect and share how we’re helping clients turn complexity into clarity—and smart buildings into smarter business.
Check out our free Risk Report to see how secure your building is: https://intelligentbuildings.com/risk-report/